Yi IoT Home Camera Riddled with Code-Execution Vulnerabilities
4.5 (710) · € 13.99 · En stock
Five of them allow remote compromise of the IoT gadgets, so attackers can intercept video feeds and more.
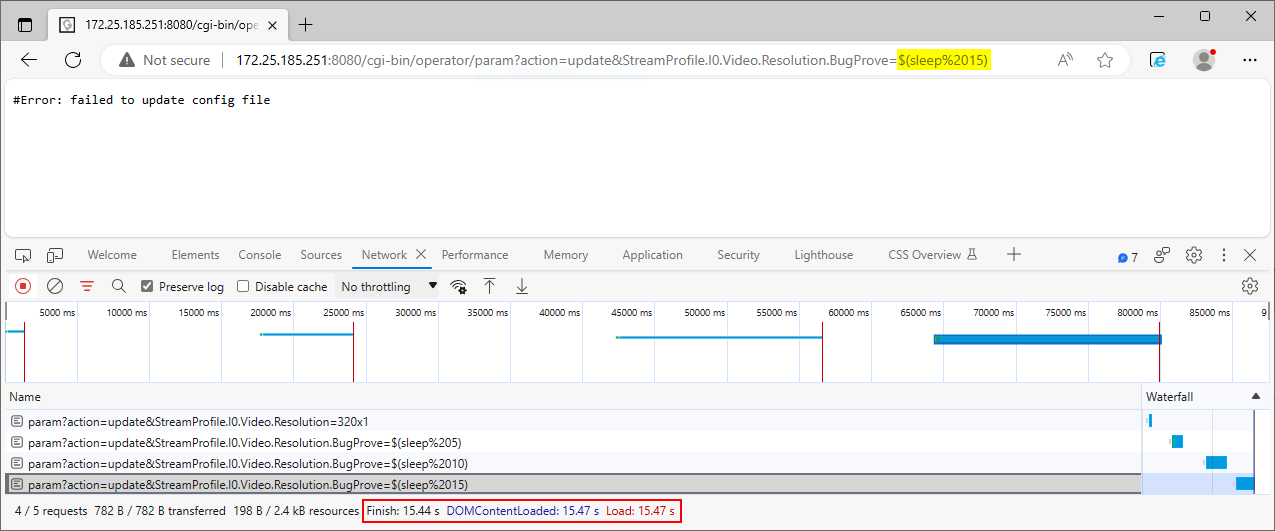
IoT Bug Hunting - Part 2 - Walkthrough of discovering command injections in firmware binaries
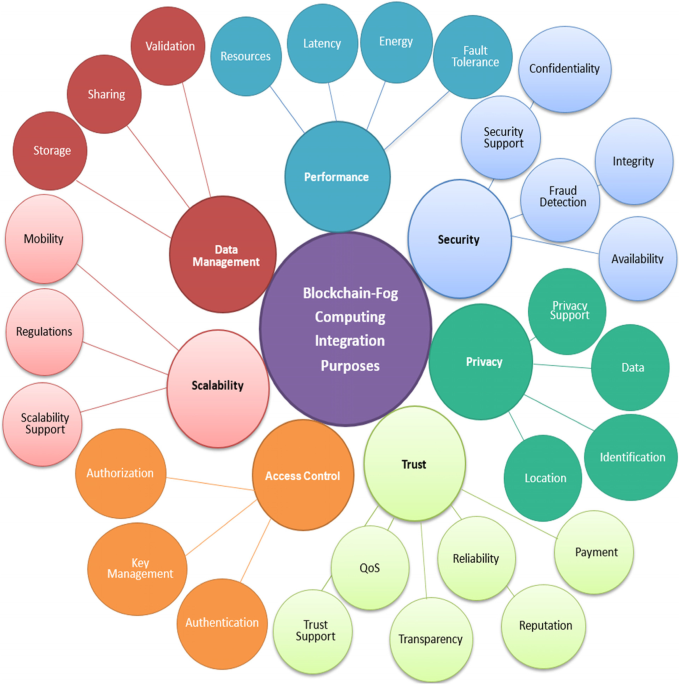
A systematic review of the purposes of Blockchain and fog computing integration: classification and open issues, Journal of Cloud Computing

Simple Remote Code Execution Vulnerability Examples for Beginners, by Ozgur Alp

Remote-code-execution-via-server-side-prototype-pollution

Yi IoT Home Camera Riddled with Code-Execution Vulnerabilities

White Paper SecurityThreats, PDF, Computer Network

Calaméo - 3c Tecnologia Ed44 Vol12 N2

Weaver E-cology OA System Remote Code Execution Vulnerability Threat Alert - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Misha Suresh, Author at WiDS Worldwide

Fog computing for next-generation Internet of Things: Fundamental, state-of-the-art and research challenges - ScienceDirect

A systematic review of the purposes of Blockchain and fog computing integration: classification and open issues, Journal of Cloud Computing











